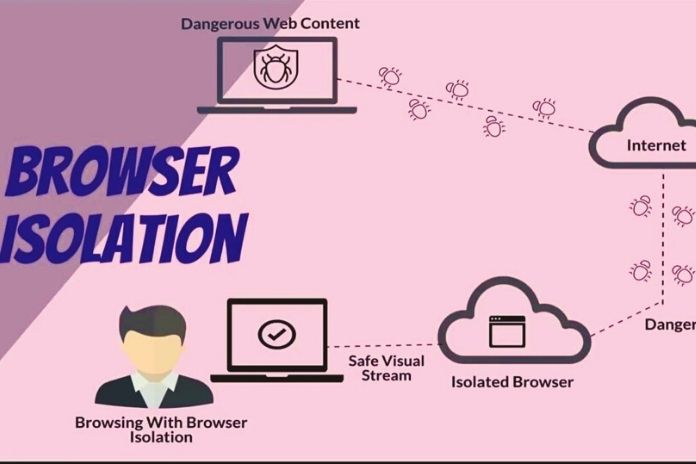
Browser Isolation: Employees use web browsers for many different tasks, but companies must expect that they will. Endpoint security solutions, and secure web gateways can block many avenues of attack, but not all. Browser isolation ensures that all internet activity takes place in a virtual environment in the data center. IT departments let hackers with browser isolation go nowhere. We would be delighted if you could use this non-exclusive article in whole or in part for editorial purposes – free of charge, of course. As always, we are happy to answer any questions you may have.
Browser Isolation: Protection Against Malicious Web Content
Whether cat videos, Facebook, webmail, online research or business applications: Employees use browsers for an endless number of activities, whether they are related to work or not. Companies have to expect a colleague to come across malicious or manipulated content or click carelessly. This is not even a problem if the infrastructure for it is set up properly. But if this malicious content is executed on the end device, the damage can be immense, and the attackers can enter the network.
Few administrators rightly trust the inherent security of web browsers and the associated plug-ins. At the same time, end users demand access to various internal and external web resources and love the convenience of the little add-on programs in the browser. Restricting access to this universe of content is, in many cases, unrealistic, but special protection is advisable. The group of people who urgently need it in the face of today’s threat landscape include board members and employees in the HR or finance department. Use scenarios that require special protection include the use of legacy applications and untrustworthy online sources and websites.
Organizations that are concerned about the security of their browsers can do something. The simple basic idea is to virtualize the browser, to decouple it from the end-user system completely and to protect the isolated environment with the latest options for securing virtual systems – even if an attack should be successful in the first step or malware could gain a foothold – it cannot escape from its cage and cause no harm.
Why Are Browsers Unsafe?
But first to the question of why browsers are so insecure. Couldn’t it just be made safe? The problem is that web browsers are designed to download very heterogeneous rich content and run some of it locally to render web pages and content. This content execution represents a risk because attackers exploit weaknesses in browsers and the extremely large variety of common plug-ins. This can lead to the compromise of the end device and the installation of ransomware or other malware.
Hackers can attack and spy on the neighboring infrastructure in the network. For example, APTs (Advanced Persistent Threats) prefer to use browsers as a gateway to infect organizations. This often happens through vulnerabilities in plug-ins such as Adobe Flash, Adobe Reader or Java.
Step 1: Protection Through Endpoint Security And Secure Web Gateways
Most companies use Endpoint Anti-Malware and Secure Web Gateways (SWG) to protect against browser-based attacks. They remain a necessary part of the security infrastructure. Today’s anti-malware searches for known and unknown malware, monitors processes, uses numerous other security mechanisms such as machine learning and fends off most attacks. But even the best solutions cannot prevent new, sophisticated approaches from sometimes slipping through the cracks. An example of this is the seemingly legitimate execution of a compromised program after identity theft.
Likewise, a Secure Web Gateway, which restricts surfing to known good web resources, is not a complete solution. Maintaining the list of legitimate resources is a hassle, even for a small business. Because the resources that end-users need are long and dynamic, even a trusted website can be compromised in several ways, turning a good resource into malicious in no time. Even using a hybrid approach, like URL Reputation, always remains reactive by definition.
Step 2: Protection Through Browser Isolation
A necessary second step is, therefore, the isolation of browsers (browser isolation). This means that the principle of the demilitarized zone (DMZ) is applied to the browser: Administrators have long been designing data centers in such a way that they isolate web-based resources, such as web servers, in the DMZ. More sensitive resources, such as application and database servers, are hosted in parts of the network that are not directly accessible from the outside.
Many companies use the same concept for web browsers: since browsers are outward-facing resources, they should be isolated from end-user devices. Application virtualization is a great way to move the epicenter of browser activity from endpoints to virtualized servers. Isolating the end-user browser from the web ensures that attackers cannot gain access to the infrastructure via the browser and cannot leave the execution environment of the virtualized browser.
Step 3: Protect Virtualized Browsers From The Hypervisor
Isolating a browser is a great second step in security. But just as administrators do not leave systems in the DMZ unprotected, the systems on which virtualized browsers run and the browsers themselves must also be protected. New approaches use the unique opportunity to secure virtual instances from the hypervisor.
This is no longer about looking for good or harmful elements, as with other security mechanisms. A browser environment protected in this way defends against attacks by observing attack techniques such as buffer overflow, code injection, and heap spray from the server’s main memory, which makes the browser available in a virtualized manner. These are the techniques with which many attacks begin and are recognized employing sophisticated technology directly in the raw memory and are stopped before execution.
Because the solution protects the virtual machine from the outside, the attacker cannot recognize it or defeat it. Without a client or other resources on the protected Virtual Apps servers, this security approach detects attack techniques that aim to exploit known, unknown and new types of vulnerabilities in web browsers and the associated plug-ins.
Citrix is one of the providers of virtualized and, at the same time, user-friendly provision of browsers, whose products are used in many speaking companies. This company’s hypervisor was also the first to enable the use of the Hypervisor Introspection (HVI) developed by Bitdefender, thereby permitting completely secure browser isolation. With the combined approach of these technologies, browsers no longer offer any attack surface.
Browser Isolation: Let The Hacker Run Wild
Web browsers are one of the most important gateways for malware and hacker attacks. Endpoint Security and Secure Web Gateways block many avenues of attack, but not all. Browser isolation ensures that all browser activity takes place in a virtual environment in the data center. It can be protected with the most modern means, particularly with hypervisor introspection (HVI).
Such specially secured browser isolation is ideal for top management, finance and human resources, and high-risk resources and outdated browsers that have to remain in use to support legacy applications. If employees are tempted to click on a cute cat video again, that’s only a case for controlling, but it is no longer for IT security. Because the hacker runs into nowhere: There is nothing to be gained from where he is.
ALSO READ: DevSecOps: 7 Tips To Get You Started Quickly